Breach Attack Simulation (BAS) Services from CyberNX
Talk to our Experts Today
INTRODUCTION
CyberNX - Your Breach Attack Simulation Exercise Partner

We address your key challenges
How It Works?
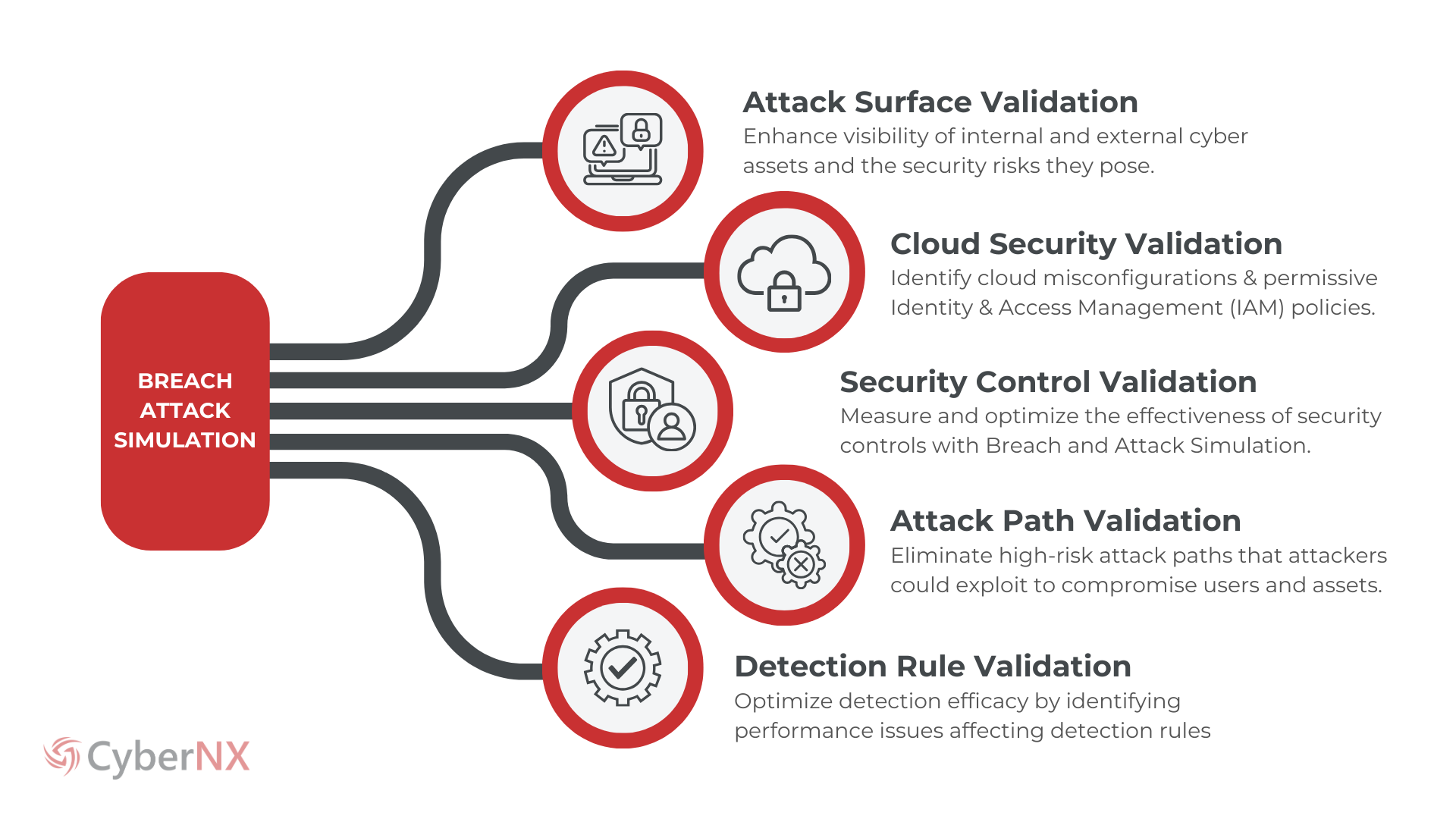
APPROACH
Why CyberNX for Breach Attack Simulation Services?
01
Initial Consultation
02
Environment Assessment
03
Scenario Development
04
BAS Execution
05
Analysis & Reporting
06
Post-Exercise Consultation
Looking to test your Cyber Defense Capabilities? Contact Us for Conducting a Comprehensive Breach Attack Simulation Exercise.
BENEFITS
Comprehensive Breach Attack Simulation (BAS) Service
Customized Security Insights
Gain tailored cybersecurity insights through initial consultations that align BAS exercises precisely with your organization’s security objectives and challenges.
Comprehensive Risk Mitigation
Identify and mitigate vulnerabilities across all IT domains—from cloud environments and applications to servers, endpoints, and APIs—ensuring robust defence against diverse cyber threats.
Optimized Resource Utilization
The results can be used to fine-tune security tools to optimize its performance and effectiveness, maximizing the effectiveness of your cybersecurity investments.
Proactive Threat Management
Improve monitoring capabilities to detect and respond swiftly to emerging threats, enhancing your organization’s resilience and minimizing potential impacts of cyber breaches.
Continuous Improvement
Results and recommendations helps organisations to improve effectiveness of cybersecurity posture.
TESTIMONIALS
Hear from Our Satisfied Clients about CyberNX
“Best partners you can find for your Cloud Security journey.”
As a CISO what you look for a partner is passion, zeal and ownership for the project. I found all this in our work with Cyber NX, a niche firm specialising in Cloud Security. When I was looking for someone to audit our Cloud environment and make a roadmap for enhancing security I found a lot of vendor who shared high level frameworks. However, it was CyberNX who gave a specific and detailed gap assessment methodology. Their final report and roadmap helped us improve our Cloud Security posture and mitigate critical risks. CyberNX and their founder Bhowmik Shah are the best partners you can find for your Cloud Security journey.

“Best partners you can find for your Cloud Security journey.”
As a CISO what you look for a partner is passion, zeal and ownership for the project. I found all this in our work with Cyber NX, a niche firm specialising in Cloud Security. When I was looking for someone to audit our Cloud environment and make a roadmap for enhancing security I found a lot of vendor who shared high level frameworks. However, it was CyberNX who gave a specific and detailed gap assessment methodology. Their final report and roadmap helped us improve our Cloud Security posture and mitigate critical risks. CyberNX and their founder Bhowmik Shah are the best partners you can find for your Cloud Security journey.

“Best partners you can find for your Cloud Security journey.”
As a CISO what you look for a partner is passion, zeal and ownership for the project. I found all this in our work with Cyber NX, a niche firm specialising in Cloud Security. When I was looking for someone to audit our Cloud environment and make a roadmap for enhancing security I found a lot of vendor who shared high level frameworks. However, it was CyberNX who gave a specific and detailed gap assessment methodology. Their final report and roadmap helped us improve our Cloud Security posture and mitigate critical risks. CyberNX and their founder Bhowmik Shah are the best partners you can find for your Cloud Security journey.

For Customized Plans tailored to Your Needs,
Get in Touch Today!
RESOURCES
Cyber Security Knowledge Hub
BLOGS
CASE STUDIES
DOWNLOADS
FAQ