Cloud Security Assessment by Specialists
Request a Free Consultation
INTRODUCTION
Cloud Security Assessment and Remediations with CybeNX Specialists

We address your key challenges:
How It Works?
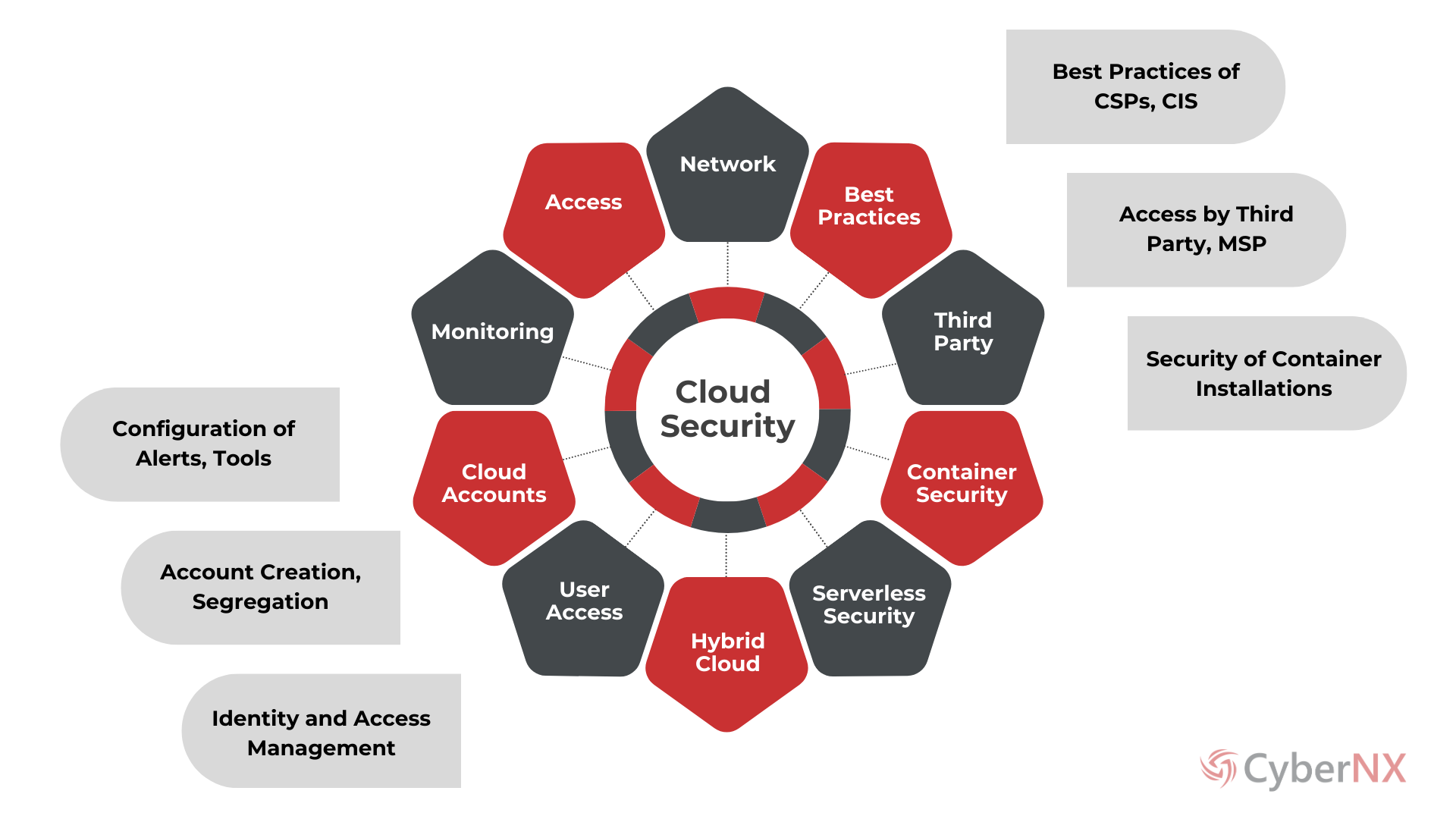
APPROACH
Why CyberNX for Cloud Security Assessments?
01
Cutting-Edge Tools
02
Client-Centric Approach
03
Risk Mitigation
04
Actionable Insight
05
Regulatory Compliance
Looking for Cloud Security Assessment Services? Connect with our Team of Cloud Security Specialists!
BENEFITS
Deep Visibility into Your Cloud Security and Compliance
Highly Specialised Professionals
We have a team of cloud security specialists experienced in securing diverse cloud environments across various industries.
Comprehensive Security Evaluation
We meticulously examine configurations, access controls, network architecture, and data storage to identify vulnerabilities.
Technical Insights and Recommendations
We provide actionable technical insights and tailored recommendations, including configuration adjustments, access control enhancements, encryption, and threat mitigation strategies.
Enhanced Incident Response Preparedness
We help you strengthen your incident response strategies, improve response times, and minimize incident impact on operations.
Documentation and Reporting
We provide detailed reports summarizing findings, recommendations, and remediation steps for stakeholders, IT teams, and auditors.
TESTIMONIALS
Hear from Our Satisfied Clients about CyberNX
“Best partners you can find for your Cloud Security journey.”
As a CISO what you look for a partner is passion, zeal and ownership for the project. I found all this in our work with Cyber NX, a niche firm specialising in Cloud Security. When I was looking for someone to audit our Cloud environment and make a roadmap for enhancing security I found a lot of vendor who shared high level frameworks. However, it was CyberNX who gave a specific and detailed gap assessment methodology. Their final report and roadmap helped us improve our Cloud Security posture and mitigate critical risks. CyberNX and their founder Bhowmik Shah are the best partners you can find for your Cloud Security journey.

“Best partners you can find for your Cloud Security journey.”
As a CISO what you look for a partner is passion, zeal and ownership for the project. I found all this in our work with Cyber NX, a niche firm specialising in Cloud Security. When I was looking for someone to audit our Cloud environment and make a roadmap for enhancing security I found a lot of vendor who shared high level frameworks. However, it was CyberNX who gave a specific and detailed gap assessment methodology. Their final report and roadmap helped us improve our Cloud Security posture and mitigate critical risks. CyberNX and their founder Bhowmik Shah are the best partners you can find for your Cloud Security journey.

“Best partners you can find for your Cloud Security journey.”
As a CISO what you look for a partner is passion, zeal and ownership for the project. I found all this in our work with Cyber NX, a niche firm specialising in Cloud Security. When I was looking for someone to audit our Cloud environment and make a roadmap for enhancing security I found a lot of vendor who shared high level frameworks. However, it was CyberNX who gave a specific and detailed gap assessment methodology. Their final report and roadmap helped us improve our Cloud Security posture and mitigate critical risks. CyberNX and their founder Bhowmik Shah are the best partners you can find for your Cloud Security journey.

PLANS
Cloud Security Assessment Areas
Cloud Security Assessment |
Description |
Access Controls |
Evaluation of user authentication, authorization mechanisms, and access privileges to ensure only authorized individuals can access resources. |
Network Security |
Analysis of network architecture, segmentation, firewalls, and intrusion detection systems to prevent unauthorized access and data exfiltration. |
Data Encryption |
Assessment of data encryption methods and key management practices to protect data at rest and in transit from unauthorized access. |
Identity and Access Management |
Review of identity lifecycle management, multi-factor authentication, and role-based access control to ensure proper user identity verification and access control. |
Configuration Management |
Examination of cloud service configurations to ensure adherence to security best practices and mitigate misconfiguration risks. |
Logging and Monitoring |
Evaluation of logging mechanisms, event monitoring, and anomaly detection systems to detect and respond to security incidents promptly. |
Incident Response |
Assessment of incident response plans, procedures, and team readiness to effectively mitigate and recover from security breaches. |
Compliance and Regulatory Requirements |
Verification of compliance with industry regulations and standards such as RBI, SEBI, IRDA, GDPR, PCI DSS, and adherence to organizational policies. |
Threat Detection and Prevention |
Implementation of threat intelligence feeds, malware scanning, and security analytics to identify and mitigate security threats in real-time. |
Security Training and Awareness |
Review of employee security awareness training programs to educate staff on security best practices and mitigate human-related security risks. |
Disaster Recovery and Business Continuity |
Evaluation of backup and recovery processes, redundancy measures, and continuity plans to ensure data resilience and business continuity in the event of disasters. |
Vendor Risk Management |
Assessment of third-party vendor security practices and contracts to mitigate risks associated with outsourcing cloud services. |
For Customized Plans Tailored to Your Needs,
Get in Touch Today!
RESOURCES
Cyber Security Knowledge Hub
BLOGS
CASE STUDIES
DOWNLOADS
FAQ